Illumio Insights + Check Point: Unified Visibility and Threat Detection
In today’s cloud-first world, security teams don’t suffer from a lack of data — they’re buried in it.
Alerts stream in from every direction, logs pile up, and tools fight for attention. Yet with all this information, critical threats can still go undetected until it’s too late.
The problem is a shortage of connected visibility. Perimeter tools can spot what’s coming in or going out, but not what’s moving inside. Lateral visibility tools can identify internal movement, but without knowing what happened at the perimeter, the picture is incomplete.
That’s why Illumio and Check Point have joined forces to build a joint solution.
This integration bridges the gap between perimeter defense intelligence and lateral traffic visibility. This makes threat detection more accurate, faster, and more actionable, all while helping teams get more value from their existing security investments.
Illumio Insights + Check Point: a unified approach to threat detection
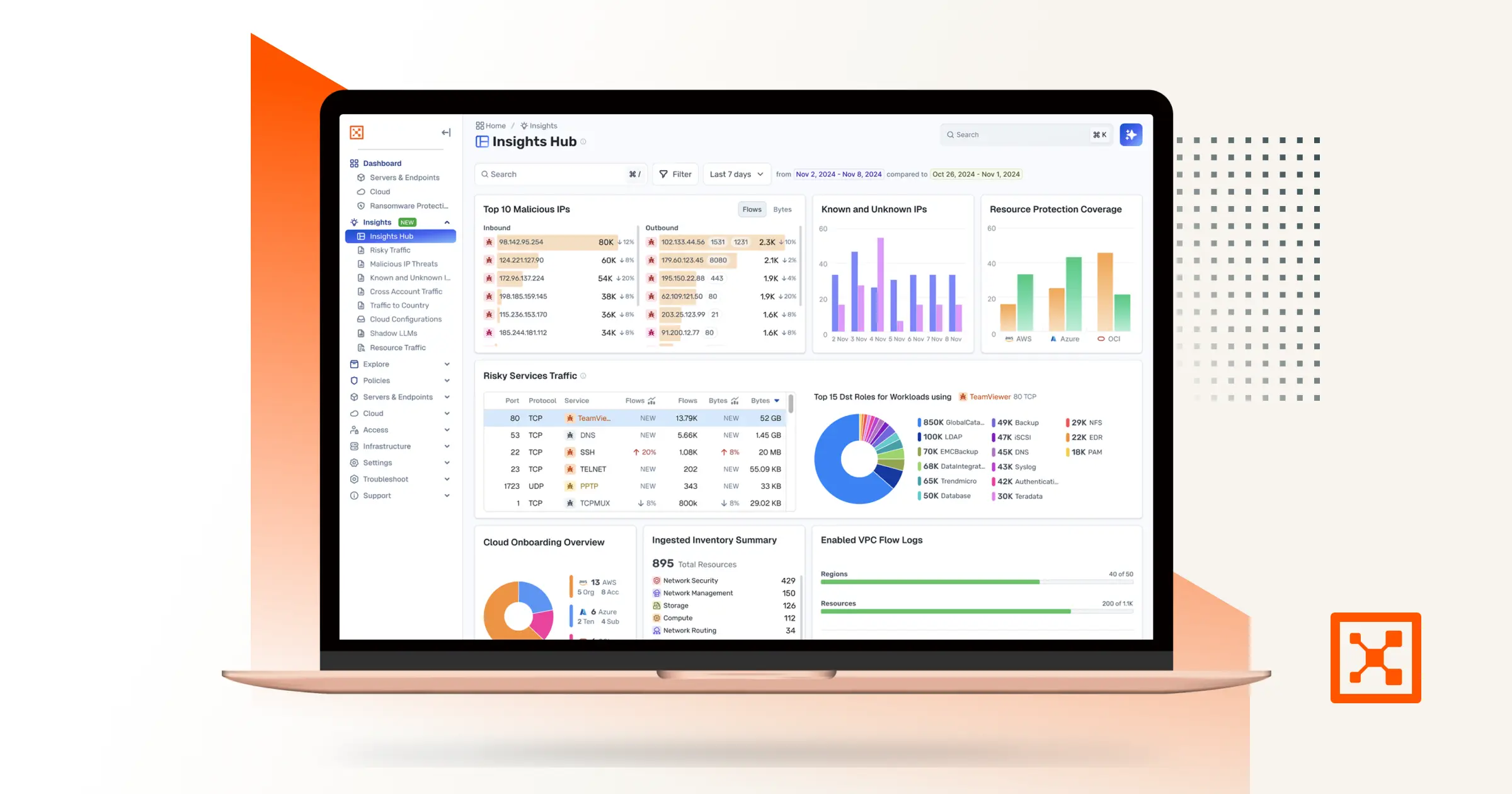
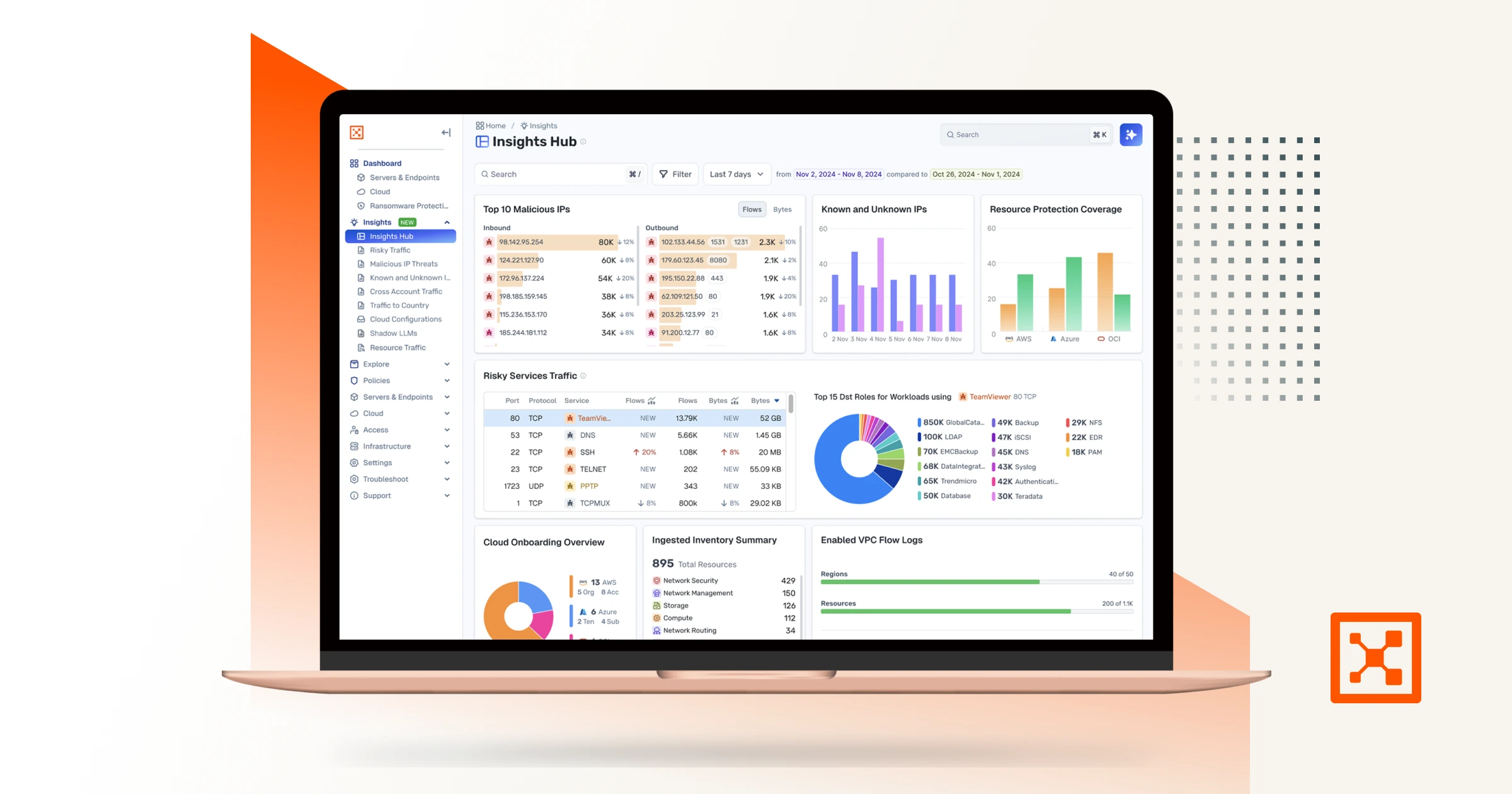
By combining Check Point’s firewall telemetry with Illumio’s workload-to-workload visibility, organizations can uncover hidden risks, reduce alert fatigue, and strengthen both detection and response capabilities.
仕組みは次のとおりです。
- Check Point firewalls collect detailed traffic logs, including connection attempts, policy matches, and threat detections.
- These logs feed directly into Illumio Insights, where they’re correlated with real-time internal traffic patterns.
- Security teams can use pre-built dashboards to spot issues like misconfigurations, anomalous communication patterns, and potential data exfiltration — all with the context needed to act quickly.
The result is a clearer, more complete view of both perimeter and internal activity, enabling better decision-making and faster containment of threats.
3 key benefits of the Illumio Insights + Check Point integration
The Illumio Insights and Check Point joint solution gives you a practical, operational advantage for detecting threats.
Here are three ways you’ll benefit from this integration:
1. Get the context you need to detect threats faster
Perimeter alerts on their own can be incomplete, making it difficult to connect them to suspicious behavior inside the network.
By correlating Check Point firewall logs with Illumio’s lateral traffic visibility, teams can detect:
- Lateral movement that signals a breach in progress
- Unauthorized communications between workloads
- Early indicators of malicious activity
This context allows for faster, more confident threat detection before the damage escalates.
2. Unify perimeter and lateral security
Firewalls excel at identifying inbound and outbound traffic, but they can’t see what’s happening between workloads inside your environment.
Illumio Insights fills that gap.
The integration delivers a single-pane-of-glass view into both perimeter and internal traffic. With this full picture, analysts can prioritize remediation efforts based on complete risk context, not just isolated events.
3. Reduce alert fatigue and speed response
Analysts waste valuable time chasing false positives or reconciling data from unconnected systems.
Illumio Insights filters and enriches Check Point alerts to surface only high-confidence, actionable threats.
This reduces noise, highlights the severity of risks, and shows exactly who’s communicating with whom, making it easier to focus on the alerts that truly matter.
Why you need connected visibility inside and outside your network
Perimeter security is essential. Firewalls, IPS, and gateways catch what’s coming in and going out.
But in today’s threat landscape, attackers will inevitably get inside your network perimeter. Perimeter security isn’t enough.
Once an attacker gets inside, perimeter tools often lose sight of the threat. That’s when the real damage happens: lateral movement between workloads, unauthorized access to critical systems, and hidden data exfiltration.
The problem is that perimeter and internal visibility usually live in separate tools. That means separate alerts, siloed data, and a fragmented view of the attack.
Security teams have to stitch the story together manually, slowing response and risking blind spots.
A joint solution like Illumio Insights and Check Point closes that gap. Check Point logs give you the “front door” view: connection attempts, policy matches, and detected threats.
Illumio Insights adds the “inside view,” mapping workload-to-workload communications and spotting anomalies in real time.
Unified visibility means faster detection, smarter response, and fewer chances for attackers to hide.
Unified visibility for a faster response
Attackers are moving faster, and the time between initial compromise and lateral movement is shrinking.
Delays caused by noise, incomplete visibility, or siloed tools give adversaries the advantage.
The Illumio Insights and Check Point integration provides the clarity, context, and speed you need to keep up:
- Clarity to see both internal and external traffic in one view
- Context to prioritize threats and guide response
- Speed to detect and contain incidents before they escalate
When it comes to modern threats, every second counts. This integration helps you make those seconds matter.
開始 イルミオインサイトの無料トライアル 今日。
.png)

.webp)