Dive deeper into Illumio Zero Trust Segmentation with think pieces, Illumineer profiles, instructional guides, and more
.svg)
Cyber Resilience

The CISO’s Playbook: How DXC Is Aligning Security with Business Growth
Discover how DXC’s CISO Mike Baker uses Zero Trust, AI, and security graphs to align cybersecurity with business growth, resilience, and innovation.
.webp)
Mapping the Future: Why Cybersecurity Visibility is the Greatest Advantage
Learn why CISOs must think like mapmakers to master cloud security, AI risks, and systemic threats.
.webp)
How Illumio Helps Federal Agencies Secure Mainframes
Learn how Illumio helps federal agencies meet Zero Trust and BOD mandates by securing mission-critical legacy systems at scale.
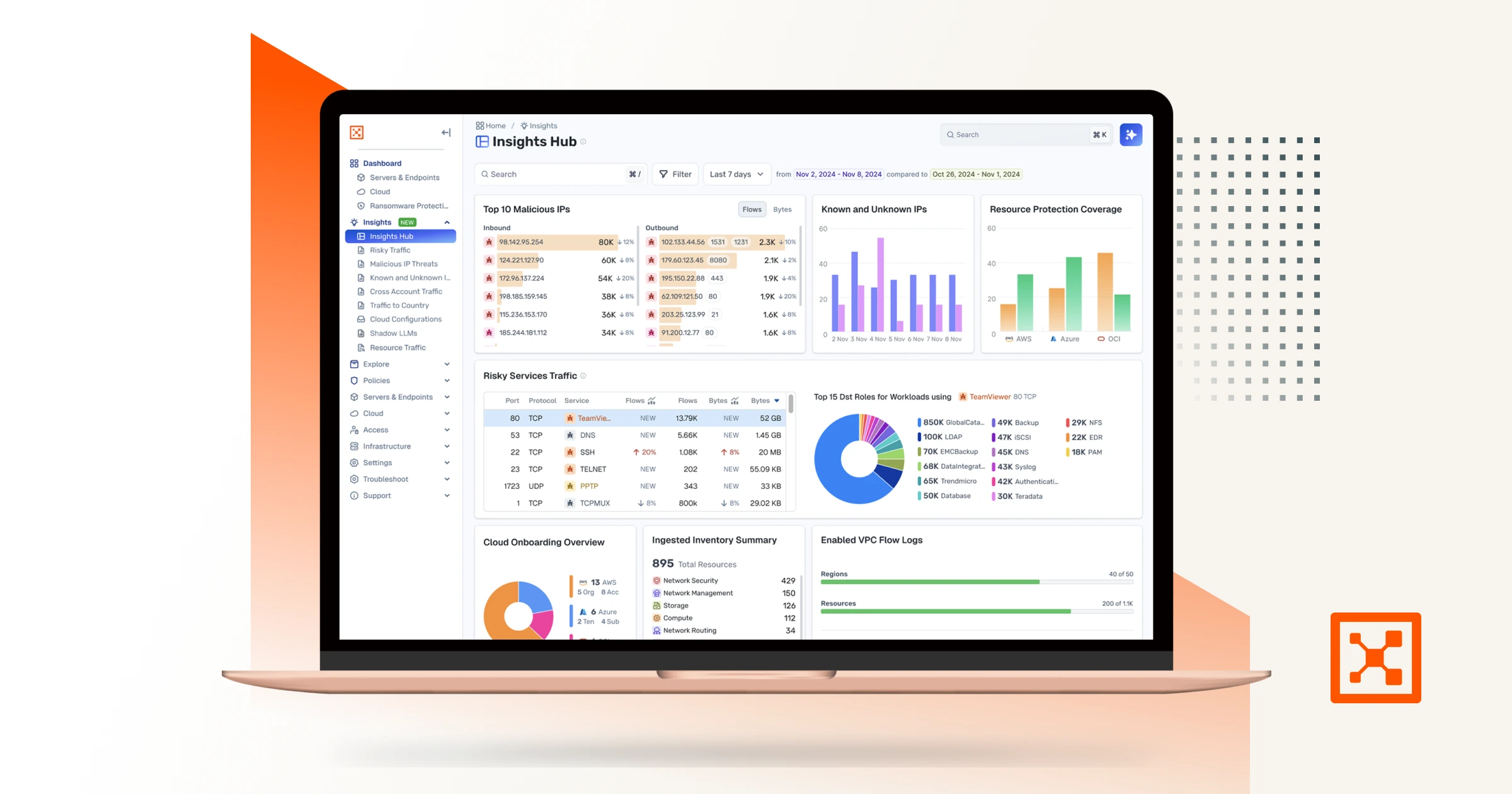
How AI Security Graphs Are Changing Cloud Detection and Response
Discover how AI security graphs power cloud detection and response (CDR) to detect lateral movement, spot risk, and stop breaches before they spread.

Cyber Insurance Is Getting Stricter: Here’s How Illumio Helps You Keep Up
Learn how Illumio helps you reduce risk, contain breaches, and prove resilience to secure better coverage and lower premiums.
.webp)
The CISO’s Playbook: Why You Need to Make Security Risk a Business Metric
Learn why today’s CISOs must bring data to the boardroom to prove risk reduction, gain budget support, and align cybersecurity with business goals.

How Security Graphs Turn Cyber Noise Into Real Risk Action
Discover how security graphs transform raw data into real-time insight, helping security teams detect lateral movement, prioritize risk, and clearly communicate threats to the board.

ToolShell: CISA’s Warning to Federal Agencies About a New Remote Code Execution Vulnerability
Discover how federal agencies can respond to ToolShell, a critical SharePoint RCE vulnerability, with breach containment strategies.

Welcome to the Post-Breach Era. Is Your Cyber Strategy Ready?
Discover why cybersecurity leaders must shift from prevention to resilience as Illumio CEO Andrew Rubin explains how to thrive in the post-breach world with Zero Trust, AI, and security graphs.
%20(1).webp)
Forget AI Moonshots. Focus on Automating the Boring Stuff First.
Learn why the real value of AI in cybersecurity comes from automating the boring stuff and how Illumio Insights helps.
.webp)
What U.S. Army and Navy SEAL Strategies Can Teach You About Zero Trust
Learn how military principles like terrain, visibility, and preparation offer a new lens for building resilient cybersecurity strategies.

Here Be Dragons: The Growing Cyber Threats to Critical Infrastructure
Discover how cyberattacks on critical infrastructure are rising in 2025 as global tensions grow and state-backed groups target utilities, healthcare, and more.
Assume Breach.
Minimize Impact.
Increase Resilience.
Ready to learn more about Zero Trust Segmentation?